Marking Tech: Cybercrime vs. Middle Market
Cybercrime has become an increasingly prevalent threat in today’s digital landscape, affecting businesses of all sizes. While large corporations often make headlines when targeted by cyberattacks, small businesses are not immune to the detrimental effects of these crimes. In fact, they are particularly vulnerable due to limited resources and cybersecurity measures. According to recent statistics, there have been a staggering 832 reported cybercrime incidents, with 130 of them resulting in confirmed data closure. In this article, we will investigate the impact of cybercrime on small businesses, exploring the frequency of attacks, common patterns, threat actors involved, their motives, and the types of data most commonly compromised.
1. Frequency of Attacks
Small businesses face a constant barrage of cyberattacks, with a staggering 832 incidents reported recently. This alarming number highlights the scale of the problem and emphasizes the urgent need for robust cybersecurity measures. These attacks can disrupt business operations, compromise sensitive data, and lead to financial losses. Small businesses, often lacking dedicated IT departments or comprehensive security strategies, are attractive targets for cybercriminals seeking easy prey.
2. Common Patterns
System intrusion, social engineering, and privilege misuse emerge as the top patterns observed in cybercrime incidents, accounting for 98% of breaches. System intrusion involves unauthorized access to a business’ network or computer systems, allowing hackers to exploit vulnerabilities and gain control. Social engineering tactics, such as phishing emails or phone scams, trick employees into revealing sensitive information or granting access to confidential systems. Privilege misuse refers to the abuse of authorized access privileges by insiders, such as employees or contractors, who exploit their elevated permissions for malicious purposes.
3. Threat Actors
Cybercrime incidents involve various threat actors, with external entities accounting for 69% of breaches, internal individuals responsible for 34%, and a small percentage (3%) involving multiple actors. External threat actors, including organized criminal groups and state-sponsored hackers, target small businesses seeking financial gain or aiming to disrupt operations. Internal threats, on the other hand, can arise from disgruntled employees or individuals with privileged access who exploit their position for personal gain or revenge.
4. Actor Motives
Financial gain emerges as the primary motive behind cybercrime incidents, accounting for 100% of the breaches reported. Small businesses, often viewed as softer targets compared to larger enterprises, are targeted for their financial resources, customer data, or proprietary information. Cybercriminals seek to exploit vulnerabilities in small business security defenses to extract ransom payments, commit fraud, or sell stolen data on the dark web. The potential monetary gains, coupled with the relative ease of targeting small businesses, make them attractive targets for financially motivated threat actors.
5. Compromised Data
When it comes to the types of data compromised in cybercrime incidents, credentials top the list, accounting for 93% of breaches. Hackers target login credentials, passwords, and other authentication information to gain unauthorized access to systems or perpetrate identity theft. Internal data, constituting 4% of breaches, includes sensitive information stored within the organization, such as financial records or employee data. The remaining 3% involves the compromise of multiple types of data, ranging from customer information to intellectual property.
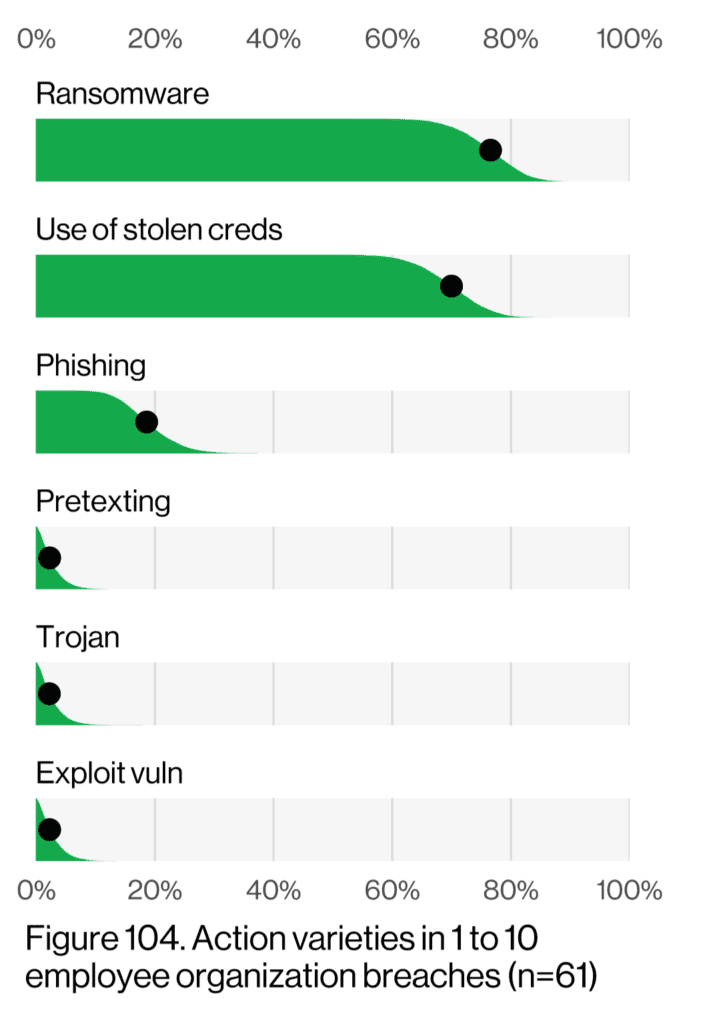
The middle market faces a unique set of challenges in today’s evolving information technology horizon. Among the numerous threats they encounter, three stand out as the most common: ransomware, the use of stolen credentials, and phishing. We will explore each of these topics in detail, providing real-world scenarios and highlighting the similarities and differences between
them.
Ransomware is a malicious software that encrypts a company’s data, rendering it inaccessible until a ransom is paid to the attacker. This threat has become increasingly prevalent, targeting middle market businesses with devastating consequences. For instance, a manufacturing company may fall victim to a ransomware attack, resulting in the complete shutdown of its production line, leading to significant financial losses and reputational damage. Ransomware attacks often exploit vulnerabilities in a company’s network, compromising sensitive data and demanding ransom payments in cryptocurrency. The commonality between ransomware and the other two threats lies in their potential to disrupt business operations and cause financial harm.
The use of stolen credentials involves cybercriminals obtaining and exploiting login credentials to gain unauthorized access to a company’s systems or accounts. This threat poses a significant risk to the middle market, as stolen credentials can be sold on the dark web, providing malicious actors with access to sensitive information. For example, an employee’s compromised credentials may grant unauthorized access to a company’s financial systems, allowing the attacker to manipulate transactions or steal funds. Similar to ransomware attacks, the use of stolen credentials can lead to financial losses and damage a company’s reputation.
Phishing is a deceptive tactic used by malicious black hats to trick individuals into revealing sensitive information, such as usernames, passwords, or financial data. Middle market companies often face sophisticated phishing campaigns, where employees receive fraudulent emails or messages that appear legitimate. Once the recipient unknowingly provides their credentials or clicks on a malicious link, the attacker gains unauthorized access to company systems or personal accounts. A common scenario involves a phishing email disguised as a legitimate request for login information, leading to compromised accounts and potential data breaches. The shared characteristic among phishing, ransomware, and stolen credentials is their reliance on social engineering techniques to exploit human vulnerabilities.
Utilization of Captive Insurance
Forming a captive insurance entity can provide significant benefits when it comes to customized insurance arrangements tailored to a company’s specific risk profile. One crucial aspect of a captive insurance entity is the ability to obtain specialized coverage for emerging and unique risks, such as cyber extortion coverage for ransomware attacks and data compromise coverage for incidents involving stolen credentials and phishing.
Having cyber extortion coverage within a captive insurance entity offers protection against the rising threat of ransomware attacks. In such coverage, the entity would define specific terms and conditions related to ransomware incidents, including the trigger for coverage and the maximum limits. For example, the coverage may encompass financial losses resulting from ransom payments, expenses associated with data recovery and system restoration, and even public relations costs to manage reputational damage. By customizing the coverage, the entity can ensure that the insurance aligns precisely with their risk appetite and potential financial exposures in the event of a ransomware attack.
Similarly, a captive insurance entity can provide data compromise coverage to address incidents involving stolen credentials and phishing. This coverage aims to protect against the financial losses, legal liabilities, and reputational harm resulting from compromised data. The entity can establish specific coverage terms and conditions, such as defining what constitutes a data compromise event, the scope of coverage for legal expenses and regulatory fines, and the extent of coverage for customer notification and credit monitoring services. With this tailored coverage, the entity can mitigate the financial impact and potential legal consequences arising from incidents involving stolen credentials and phishing attacks.
By establishing a captive insurance entity with customized insurance arrangements, companies can proactively address their specific risk profiles and emerging threats. The ability to have cyber extortion coverage for ransomware attacks allows companies to transfer the financial risks associated with such incidents, enabling them to recover from attacks more effectively. Likewise, data compromise coverage within the captive entity provides a mechanism to manage the consequences of stolen credentials and phishing incidents, reducing financial losses and protecting the company’s reputation. In both cases, the tailored coverage ensures that insurance aligns precisely with the company’s risk management strategies, enhancing their ability to navigate the evolving cybersecurity landscape.